On 12 March 2024 (scheduled), several system changes will be applied to the authentication infrastructure of UTokyo Account. These changes are intended to make multi-factor authentication, which becomes mandatory for UTokyo Account, more convenient to use. For more information on the mandatory use of multi-factor authentication, please refer to “Multi-Factor Authentication is Mandatory for UTokyo Account”.
More information systems will require @utac.u-tokyo.ac.jp when signing in
When signing in to your UTokyo Account, the 1st screen below used to appear and you could sign in with your 10-digit common ID and password, omitting @utac.u-tokyo.ac.jp in some cases. After this system change, more often the 2nd screen below will appear and you will be required to enter your “10-digit common ID + @utac.u-tokyo.ac.jp”.
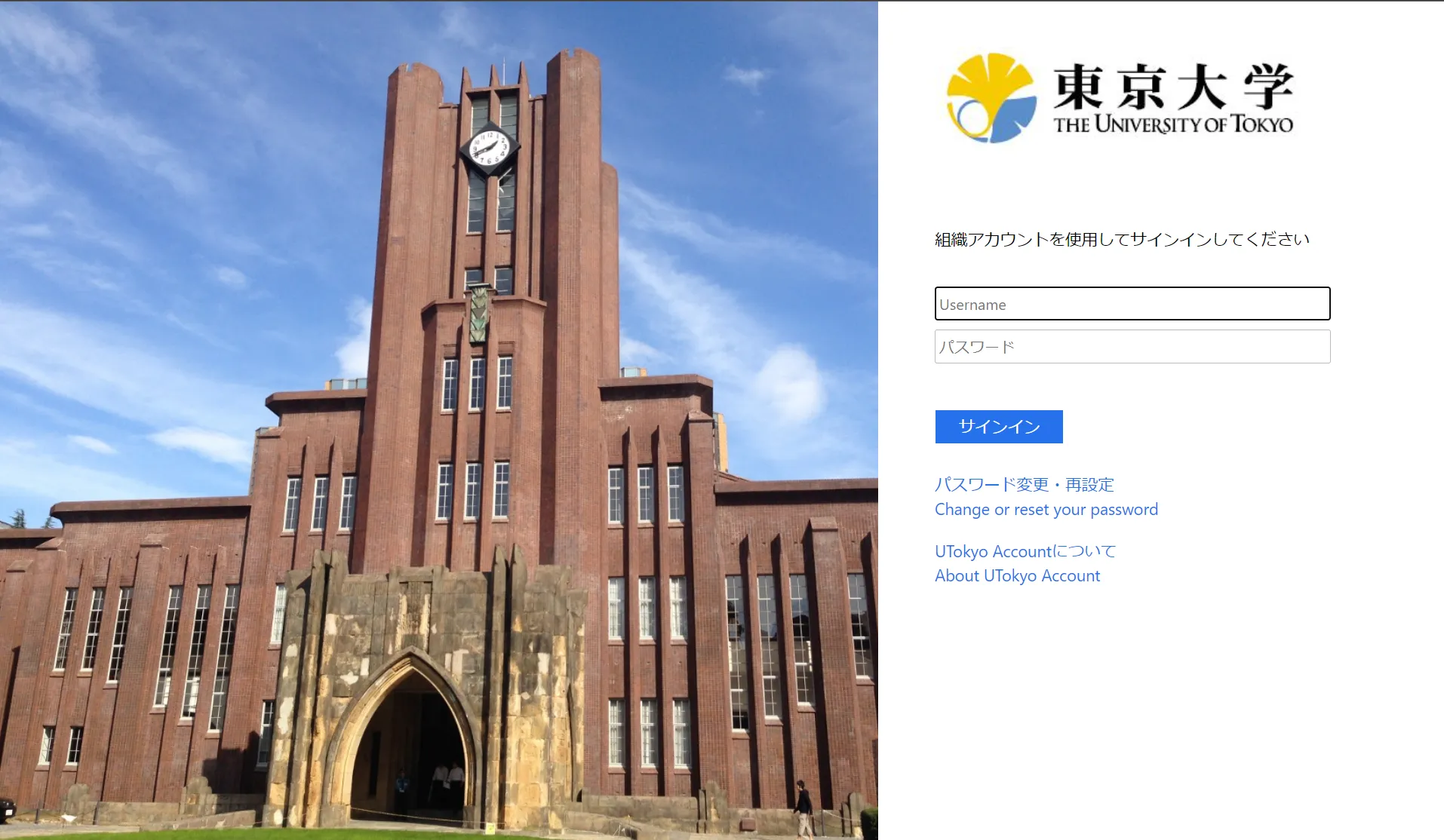
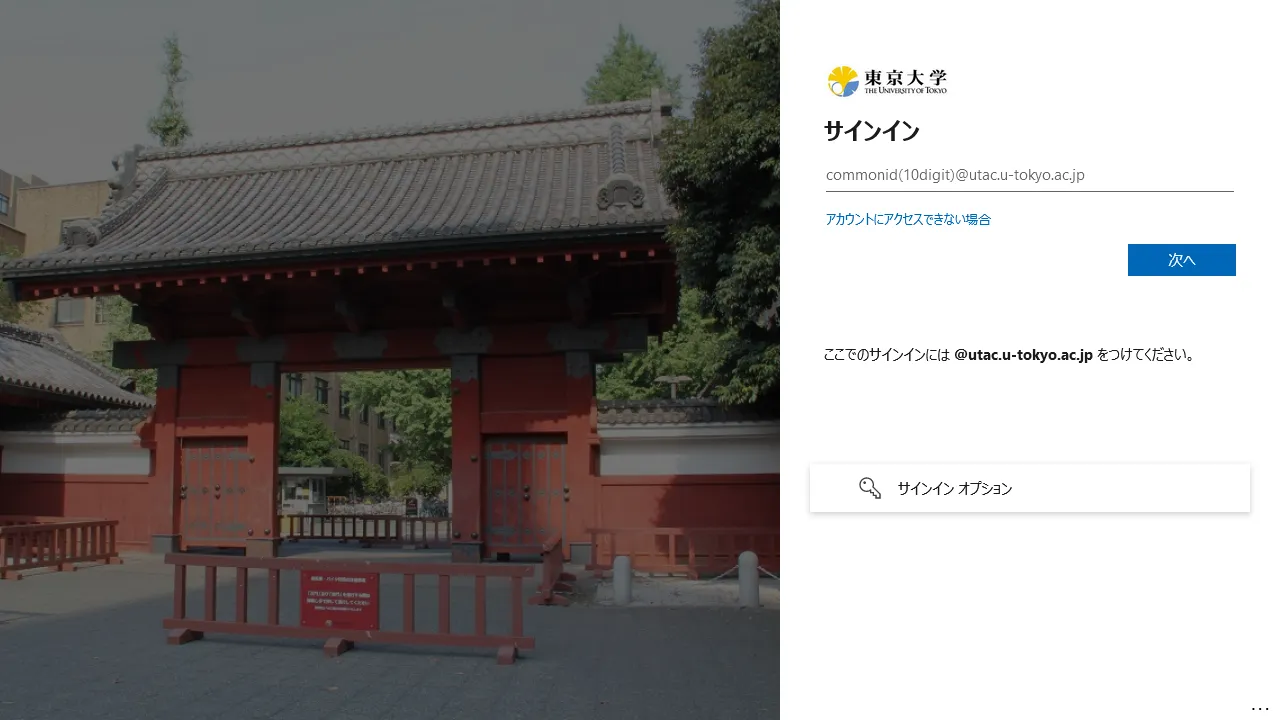
※ The 2nd screen is one that has ever been appeared, but the background image and layout will be changed on this occasion.
This change applies to information systems marked with “○” in the UTokyo Account Service Directory (in Japanese). Typical examples are as follows:
- UTAS
- UTOL
- Zoom
- ECCS Cloud Email (Google Workspace)
- UTokyo MyOPAC
- EZproxy
Please understand that this change is necessary to make passwordless sign-in widely available, which is explained next.
Passwordless sign-in will be widely available
Passwordless sign-in is signing into a system without entering a password. With this system change, passwordless sign-in will be available in many cases.
This change applies to information systems marked with “○” in the UTokyo Account Service Directory. Typical examples are as follows:
- UTAS
- UTOL
- Zoom
- ECCS Cloud Email (Google Workspace)
- UTokyo MyOPAC
- EZproxy
There are two passwordless sign-in methods available for UTokyo Account: FIDO security key and Microsoft Authenticator. Each of these methods is described below.
Please note that these passwordless sign-in methods do not require other methods of identity verification, as they alone constitute multi-factor authentication.
Using passwordless sign-in with a FIDO security key
If you are using a FIDO Security Key as your verification method for UTokyo Account’s multi-factor authentication, you can use passwordless sign-in with a FIDO Security Key. Please refer to the FIDO Security Key Initial Settings (in Japanese) for information on how to set up the initial settings and the available OS and browsers.
The sign-in process proceeds as follows:
- When the sign-in screen appears, press “Sign-in options”.
- When multiple options are displayed, select “Sign in with security key”.
- Follow the on-screen instructions to enter your PIN, complete biometric authentication or tap the security key, then sign-in is complete.
- If you are prompted to select an account, select UTokyo Account.
Using passwordless sign-in with Microsoft Authenticator
If you are using Microsoft Authenticator as your UTokyo Account’s multi-factor authentication method, you can use passwordless sign-in with Microsoft Authenticator by making an additional setting.
The setting procedure is as follows:
- If you have not registered Microsoft Authenticator as your identification method, follow the “Initial Setup Procedures for Multi-Factor Authentication for UTokyo Accounts” to register Microsoft Authenticator as your identification method.
- Launch the Microsoft Authenticator app on your smartphone and select your UTokyo Account displayed on the app.
- Press “Enable phone sign-in.”
- Press “Continue.”
- Follow the instructions to sign in.
- When you see the message “Please help us keep your device secure,” press “Register.” This completes the setup.
The sign-in process proceeds as follows:
- When the sign-in screen appears, enter your “10-digit common ID +
@utac.u-tokyo.ac.jp”. - Enter the displayed numbers into the Microsoft Authenticator app.
- Sign-in is complete.
FIDO security keys will be supported in all information systems that support multi-factor authentication
Until now, some systems that support multi-factor authentication did not support FIDO security keys. After this system change, FIDO security keys can be used in all information systems that support multi-factor authentication. The following are examples of information systems that will newly support FIDO security keys.
- UTokyo MyOPAC
- EZproxy
- Business Travel Expense System
- Academic Access Management Federation (GakuNin)